
2018 SonicWall Cyber Threat Report
Threat Intelligence, Industry Analysis and Cybersecurity Guidance for the Global Cyber Arms Race

2018 SonicWall Cyber Threat Report was gathered by SonicWall Capture Labs Threat Network which can be found on their own individual product pages or purchase them, more options can be found on individual product pages.
Security Industry Advances
Cyber Criminal Advances
State of Ransomware
Did the number of ransomware attacks last year match or exceed the frenetic pace of the year before? Or did the cyber security industry mitigate data ransom paydays? SonicWall’s real-world analysis provides contrasting numbers that tell a compelling story.
Malware Mixologists
While many innovative malware authors are no longer writing original exploits, plenty of criminals are mixing and matching code to form new “malware cocktail” strands - putting a strain on signature-only security controls.
The Encrypted Battleground
Encrypted traffic - using SSL/TLS encryption - has increased. This will mean more opportunity for threat actors to mask their attacks. But by a factor of how much?
Law Enforcement Lockdown
Governments and cyber police are cracking down. Review the key arrests made by global law enforcement and the affect they could have on future cyber attacks.
New Attack Vectors
The standard network entry points are known. But new vectors - like memory-based attacks (e.g., Meltdown) and PDF threats - will emerge as critical arenas.
Cyber Security Best Practices
A strong security posture is constantly reinforced. Gain proven tips and policies to help bolster your cyber security strategy.
Modern Threat Intelligence, Cyber Security Analysis & Advanced Malware Trends from SonicWall Capture Labs
We are engaged in a cyber arms race, pitting the cyber security industry against those who seek to profit from cybercrime.
This is a challenge we face together.
And this is the core reason SonicWall is committed to passing its findings, intelligence, analysis and research to the global public via the 2018 SonicWall Cyber Threat Report.
 Advance and retreat. Flank and charge. Ambush and assault.
Advance and retreat. Flank and charge. Ambush and assault.
The modern cyberwar - against governments, businesses and individuals alike - is comprised of a series of attacks, counterattacks and respective defensive countermeasures. Many are simple and effective. Others are targeted and complex. Yet they are all highly dynamic and require persistence, commitment and resources to mitigate. And they will not go away.
Unfortunately, organizations large and small are caught in the middle of a global cyber arms race with vastly different resources at their disposal. And while growing budgets do make a positive impact on the effectiveness against known exploits, the threat landscape evolves at such a rate that yesterday’s investment in technology could already be insufficient to deal with tomorrow’s cyber threats.
All told, there were more than 12,500 new Common Vulnerabilities and Exposures (CVE) reported in 2017 - 78 percent of which were related to network attacks.
About the SonicWall Capture Labs Threat Network
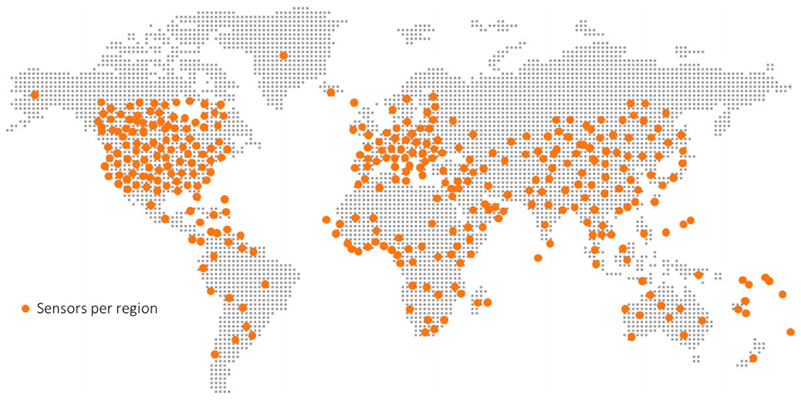
Data for the 2018 SonicWall Cyber Threat Report was gathered by the SonicWall Capture Labs Threat Network, which sources information from global devices and resources including:
- More than 1 million security sensors in nearly 200 countries and territories
- Cross‐vector, threat‐related information shared among SonicWall security systems, including firewalls, email security devices, endpoint security solutions, honeypots, contentfiltering systems and the SonicWall Capture Advanced Threat Protection multi‐engine sandbox
- SonicWall internal malware analysis automation framework
- Malware and IP reputation data from tens of thousands of firewalls and email security devices around the globe
- Shared threat intelligence from more than 50 industry collaboration groups and research organizations
- Intelligence from freelance security researchers
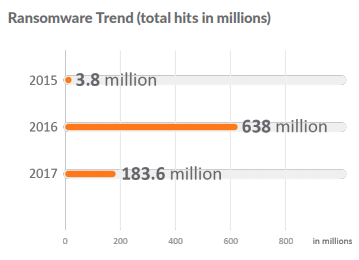
 Total Ransomware Volume Declines:
Total Ransomware Volume Declines:
If ransomware’s global impact was the major headline in 2016, its sharp decline in 2017 is just as intriguing. Even with WannaCry, Petya, NotPetya and Bad Rabbit stealing the headlines, the expectations of more ransomware attacks in 2017 simply did not materialize as anticipated. The SonicWall Capture Threat Network detected 183.6 million ransomware attacks in 2017. This marked a 71.2 percent drop from the 638 million ransomware attack events SonicWall recorded in 2016.
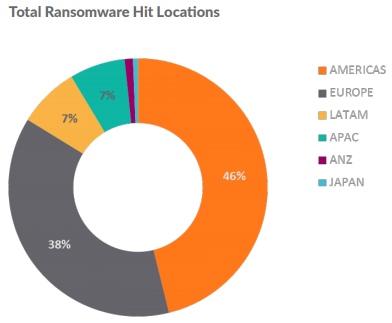
Regionally, the Americas were victimized the most, receiving 46 percent of all ransomware attack attempts in 2017. Europe saw 38 percent of ransomware attacks during that same time. Even with a decline in volume, the multi-engine SonicWall Capture Advanced Threat Protection (ATP) sandbox was responsible for identifying one new malware variant for every 250 unknown hits. Capture ATP is currently deployed at more than 30,000 organizations around the world and identifies almost 500 new malicious files each day.
SonicWall Capture ATP is automatically identifying almost 500 new malicious files each day.
By analyzing bitcoin data - the preferred currency of threat actors and cybercriminals - SonicWall researchers found that transactions via ransomware-related wallet addresses dropped in 2017.
Many organizations are also better informed and more prepared for ransomware attacks. Proactive organizations are not only building sound disaster recovery and business continuity strategies, they’re also hoarding bitcoin stockpiles - ideally when prices are lowest - as a last resort to keep business running.
Americas
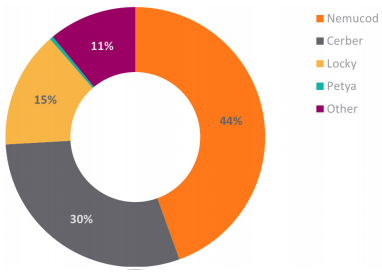
Europe
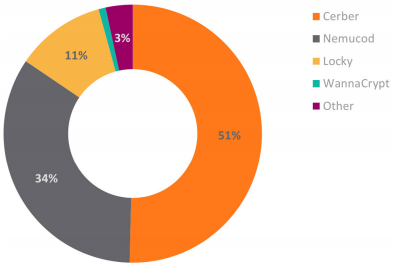
Latin America
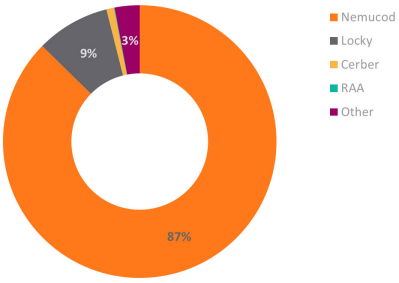
Asia Pacific
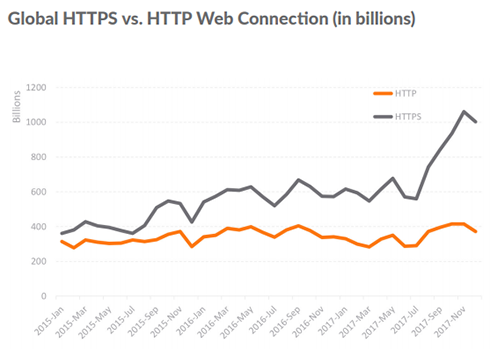
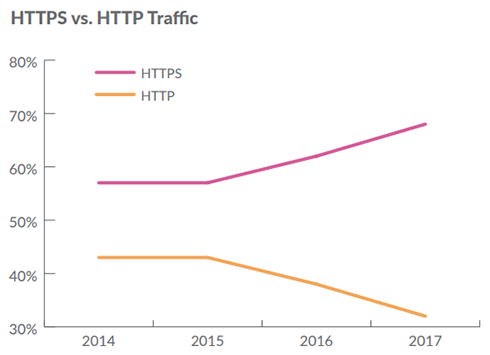
 SSL/TLS Use Increases Yet Again:
SSL/TLS Use Increases Yet Again:
The use of secure sockets layer (SSL) and transport layer security (TLS) protocols to encrypt and protect data in transit across the internet is nothing new. Until recently, encryption was typically reserved for the most sensitive web traffic (e.g., payment data, transactions, PII, etc.).
Each year, however, more and more everyday web traffic is encrypted. On March 5, 2012, Google announcedvii it was switching to HTTPS by default. Since then, SonicWall has recorded a rapid increase of HTTPS sessions in comparison to unencrypted HTTP traffic.
For analysis, SonicWall monitors the use of HTTP and HTTPS to demonstrate the increase of encrypted sessions. The graphs to the right contrast the use of each across a three-year span. The split was nearly the same at the beginning of 2015. In 2017, the use of encrypted sessions grew 24 percent over 2016 and accounted for 68 percent of overall sessions.
The acceptance of hybrid cloud environments, coupled with an explosive application-dependent society, will only accelerate the use of HTTPS in the coming years. This shift has already given more opportunity for cybercriminals and threat actors to hide malicious payloads in encrypted traffic.
In response, organizations are implementing security controls, such as deep packet inspection (DPI) of SSL/TLS traffic, to responsibly inspect, detect and mitigate encrypted attacks.
Do you have SSL/TLS inspection controls?
Encrypted traffic is a growing attack vector for cybercriminals. Unfortunately, there is a fear of complexity and a general lack of awareness around the need to responsibly inspect SSL and TLS traffic - particularly using deep packet inspection (DPI) - for malicious cyberattacks. Contact your security or firewall provider to ensure you have this capability and that it is properly activated.
 Effectiveness of Exploit Kits Impacted:
Effectiveness of Exploit Kits Impacted:
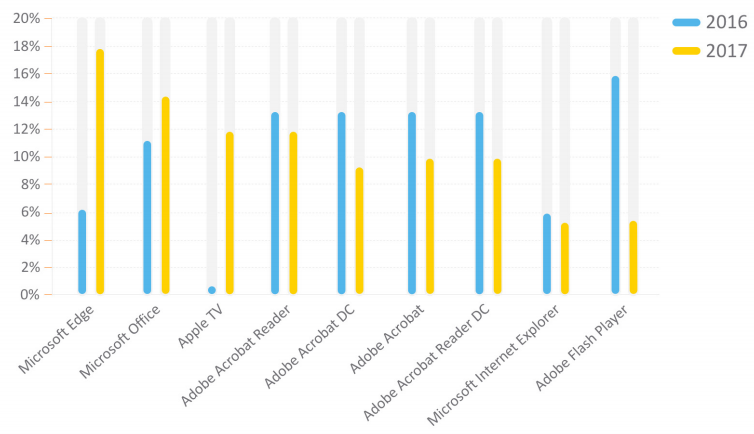
In 2016, we saw three major zero-day vulnerabilities hit Adobe Flash, which were used in multiple attacks. But since browser vendors have largely phased out Flash - it’s disabled in default browser settings - new Flash Player exploits are less attractive to attackers.
That, however, hasn’t deterred threat actors from attempting new strategies. For example, between 2016 and 2017, SonicWall found that attacks on Microsoft Edge grew 13 percent. This signifies that attacks on the vulnerable Microsoft Internet Explorer browser are in rapid decline and cybercriminals are looking for all avenues to deploy traditional exploits.
Attacks against the most popular Adobe products - Acrobat, Acrobat DC, Reader and Reader DC - were down across the board. Attacks against Microsoft Office and related applications (e.g., Word, Excel) were up nearly 4 percent.
With new applications cracking the top 10 in 2017 (e.g., Apple TV, Microsoft Office), organizations should continually redefine and broaden the scope of applications and related files that could present a risk. In analyzing application volume, machinelearning technology helps protect against newer attack vectors like Microsoft Office files, PDFs and other email-based threats.
Top Affected Applications in 2017
 Law Enforcement a Disruptive Force:
Law Enforcement a Disruptive Force:
Arrests of key malware and exploit kit authors in 2017 are now making a significant dent in the scale, volume and success of cyberattacks. While arrests in 2017 weren’t as directly tied to reducing malware attacks as in the year before, they may end up being more strategic in the long term. These efforts are helping disrupt malware supply chains and are impacting the rise of new would-be hackers and authors.
For example, in December 2017, law enforcement officials from the United States, Romania, Britain and the Netherlands collaborated to arrest five Romanian hackersviii accused of operating CTB-Locker/Critroini ransomware.
In another high-profile case, Marcus Hutchins, the British cybersecurity researcher responsible for “accidentally stopping” the notorious WannaCry ransomware attack by unknowingly activating a kill switch, was later arrested for allegedly authoring banking Trojan Kronos. If convicted, Hutchins faces six counts of hacking charges that date back to 2014 and could hold a maximum 40-year prison term.
Are arrests like these truly making an impact in the cyber arms race? Or are these simply anecdotal wins that won’t change the threat landscape? Reactive threat actor behavior in 2017 suggests law enforcement is closing in.
| Name | Nationality | Arrest Location | Status | Government Agencies | Reason |
|---|---|---|---|---|---|
| Pyotr Levashovx, xi | Russian | Russian | Seeking Extradition | Spain | Kelihos Botnet |
| Marcus Hutchinsxii | British | U.S. | Trial Pending | U.S. | Kronos Banking Trojan |
| Ruslan Stoyanovxiii | Russian | Russian | Trial Pending | Russia | Treason (Kaspersky Executive) |
| Mark Vartanyanxiv | Russian | Norway | 5 Years Prison | U.S., Norway | Citadel Malware Toolkit |
| Ytu Pinganxv | Chinese | U.S. | Trial Pending | U.S. | Sakula Malware; OPM Breach |
| Kamyar Jahanrakhshanxvi | American | U.S. | Sentence Pending | U.S. | Extortion; Attempted DDoS Attack |
| Alexandre Cazesxvii | Canadian | Thailand | Deceased | Europol, FBI, DEA, Dutch National Police | AlphaBay & Hansa Darkweb Market Operations |
| Yarden Bidanixviii | Israel | Israel | Trial Pending | Israel | vDOS Service |
| Itay Hurixix | Israel | Israel | Trial Pending | Israel | vDOS Service |
| Alexander Vinnikxx | Russian | Greece | Trial Pending | U.S., Greece, Russia | BTC-e exchange; Mt. Gox Thef |
| Identity Withheldxxi | i Ukrainian | i Ukrainian | Trial Pending | Ukraine Cyber Police | NotPetya/ExPetr Ransomware Distribution |
 Following the Bitcoin Trail:
Following the Bitcoin Trail:
Because of the inroads law enforcement agencies are making into arresting and convicting malware authors and disruptors, cybercriminals are being more careful with how they conduct business. This change is most clear in their processes for collecting data ransom payouts.
Unlike NotPetya or WannaCry ransomware, which were linked to only a handful of bitcoin wallets, most ransomware attacks in 2017 generated a unique bitcoin wallet per infection. Although still anonymous, this simple change made it more difficult to track payments received that might correlate how widespread an infection may have been.
While bitcoin and other cryptocurrencies are largely anonymous, law enforcement agencies are also cracking down on the proprietors and operators of different exchanges.
In 2017, for example, law enforcement arrested Russian Alexander Vinnik, operator of bitcoin exchange BTC-e, on more than 21 charges of money laundering, fraud and other financial crimes.
Because of this change in behavior - whether caused by law enforcement or not - it is harder to track the bitcoin earnings of specific ransomware. The majority of SonicWall ransomware analysis completed in 2017 found wallet addresses with few or no transactions at all.
Despite these findings, comparing this year’s ransomware attacks that were tied to a single bitcoin wallet (or a handful, like WannaCry’s three known wallet addresses), SonicWall has seen fewer transactions than that of the previous year’s attacks.
 More Ransomware Variants in the Wild:
More Ransomware Variants in the Wild:
This may mark a pivot point for threat actors. They’ve exhausted the capabilities of standard ransomware and need a new approach, as payouts are seemingly in decline. Despite the plunge in effectiveness, SonicWall Capture Labs recorded many more new ransomware variants, including WannaCry, NotPetya, Locky, Nemucod, Cerber, GlobeImposter,xxiii Bad Rabbit, SyncCrypt,xxiv etc.
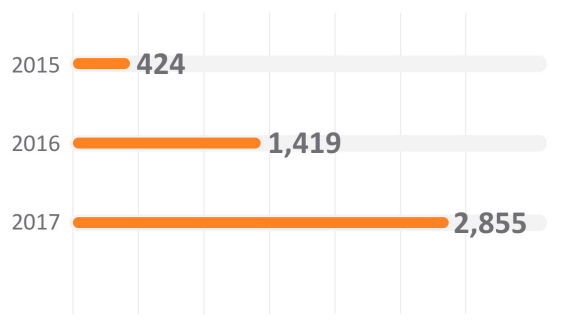
As noted earlier in the report, the total volume of ransomware was down significantly year over year. However, the number of unique ransomware variants in play increased 101.2 percent in 2017. SonicWall Capture Labs threat researchers created 2,855 new unique ransomware signatures in 2017, which was up from the 1,419 published a year before.
Ransomware draws the media lens because of its ability to successfully and simultaneously target large organizations, small businesses and even individuals. But this high profile comes with a price: awareness and understanding.
While it is just a category of malware, ransomware is about as close as it comes to a household name. So much so, organizations and individuals are educated on the matter. While apathy does still exist, some organizations are more proactive and more prepared.
Victims are less inclined to pay ransoms once infected due to the uncertainty of retrieving their files. The most malicious cybercriminals will even use ransomware like GlobeImposter, which can render a system unbootable without even requesting payment.xxv
The supposed decline in revenue is not discouraging malware authors from creating new ransomware variants, which is proven by the increasing number of ransomware signatures SonicWall created and deployed in 2017.
In addition to the new jump in variants, cybercriminals are also relying on new propagation methods (e.g., EternalBlue, Remote Desktop) in attempt to slow the decline in usefulness.
The increased popularity of ransomware as a service (RaaS) also affected the increase in variants recorded.xxvi It’s another channel strategy for authors and cybercriminals to get their “product” in the market, particularly those who want to modify someone else’s code to make a quick - albeit illegal - dollar.
Thankfully, the security industry has had several years to implement countermeasures to mitigate ransomware attacks. The period between 2013-2016 was lucrative for cybercriminals. Their sophistication and innovation paid off. It’s too soon to know if 2017 was an outlier or if 2018 will continue this downward trend, signifying a true shift in the threat landscape.
Unique Ransomware Signatures
 The Rise of IOT Ransomware
The Rise of IOT Ransomware
IoT ransomware is a type of attack against an IoT device to gain control of the device’s functionality. While many smart devices do not hold any valuable data, there is still a potential for holding an owner, business or organization ransom. xxvii
This type of attack largely depends on timing. For example, if an attacker can gain control of a business HVAC during work hours, there is a higher likelihood that they will pay the ransom.
Unfortunately, there will be more insidious cases (e.g., controlling connected cars, baby monitors, medical equipment) where victims may have no choice but to pay ransoms to regain control of critical devices or equipment.
DDoS attacks still remain the major threat to IoT devices and networks. Each compromised device could send up to 30 million packets per second to the target, creating an IoT-powered botnet that could easily launch a terabit-level DDoS attack in the future. The security of IoT devices will remain a critical topic in 2018.
Is Mobile Ransomware Next?
The mobile device is ubiquitous across all cultures, ages, regions and even incomes. It’s estimated that 6 billion mobile devices will be in circulation by 2020.xxviii With such a footprint, there’s little surprise that it would make the perfect target for a ransomware attack.
Following reports from WikiLeaks, Israeli researcher Amihai Neiderman uncovered 40 zero-day vulnerabilities of Samsung’s open-source operating system Tizen, which works on a wide range of Samsung devices.
These vulnerabilities would allow attackers to remotely control Samsung devices already on the market, such as smart TVs, smart watches and the company’s popular line of Android smartphones.xxix Because Android is the most targeted operating system, smartphones that run Android are the most targeted device.
The mechanisms used by ransomware to render victim devices useless has also shifted. Earlier attacks simply covered the entire screen with a custom message, but exploits in 2017 began to completely encrypt the device. One such attack encrypted the device and reset the lock screen security PIN. From that point, it’s easy to make the jump to holding the device for ransom.
 SSL Encryption Hiding Cyberattacks:
SSL Encryption Hiding Cyberattacks:
While encrypting traffic is a necessary practice, it does leave opportunity for threat actors. The same great protections SSL and TLS encryption afford well-meaning organizations may be leveraged to cloak illegal or malicious traffic as well.
Over time, the malware industry has improved their skillsets and are applying new and sophisticated technologies into their campaigns, including the use of encryption to hide payloads transferred over the internet.
Encryption was leveraged more than previous years, for both legitimate traffic and malicious payload delivery. However, for the first time ever, SonicWall has real-world data that unmasks the volume of malware and other exploits hidden in encrypted traffic.
Based on data from the subset of SonicWall firewalls using DPI-SSL, an average of 4.2 percent of all file-based malware propagation attempts used SSL/TLS encryption in 2017.
SonicWall Capture Labs found, on average, 60 file-based malware propagation attempts per SonicWall firewall each day. Without the ability to inspect encrypted traffic, the typical organization would have missed over 900 file-based attacks per year hidden by SSL/TLS encryption.
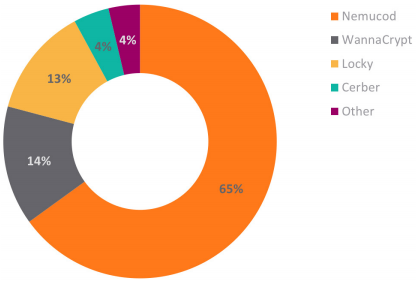
Top Encrypted Ransomware
| Name | Hits |
|---|---|
| JScript.Nemucod.BZN | 204,519 |
| JScript.Nemucod.XJ_2 | 30,972 |
| Cerber.G_17 | 5,651 |
| JScript.Nemucod.CI_3 | 906 |
| JScript.Nemucod.HM | 641 |
| Cerber.RSM | 533 |
| Locky.VBS_2 | 523 |
| JScript.Nemucod.RJ_12 | 306 |
| JScript.Nemucod.J | 257 |
IPS Attacks Over SSL by Month
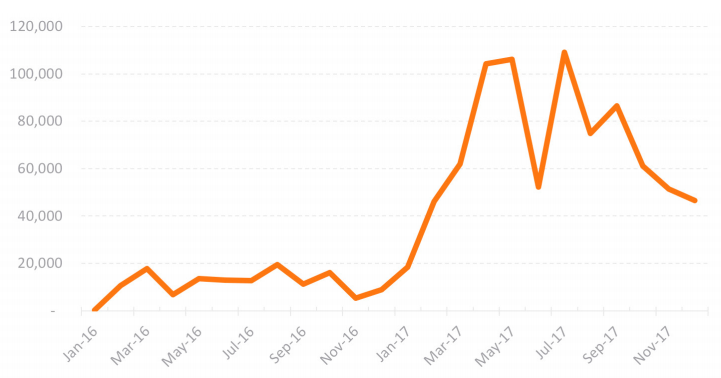
As outlined, the use of encryption to protect web traffic was up 24 percent in 2017. With this growth, each year provides cybercriminals more and more avenues for obscuring their malicious actions. For example, the use of SSL to download Nemucod content increased in 2017.
Leveraging intrusion prevention systems (IPS), SonicWall recorded and analyzed similar trends for attempted network intrusions. The top IPS attacks focus on HTTP Header, Directory Traversal and SQL Injection.
Encrypted traffic will continue to grow, but unencrypted traffic will remain for most public services. However, threat actors will continue to use encryption to hide attacks in 2018 and beyond.
In response, more organizations and enterprises are implementing SSL decryption, inspection and mitigation capabilities into their security strategy.
Malware Attacks Over SSL by Month
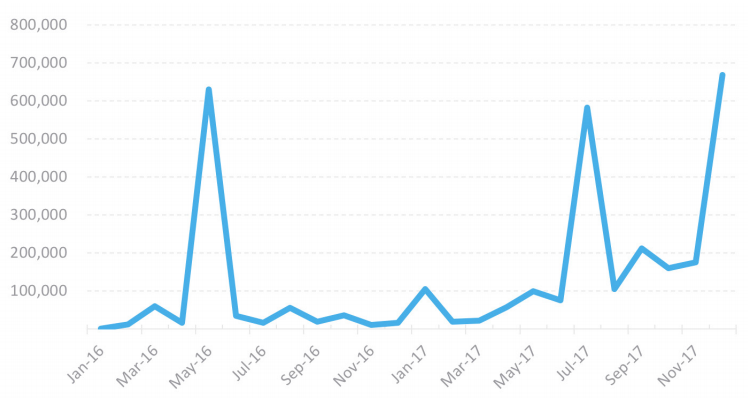
 Malware Cocktails Still Mixing Things Up:
Malware Cocktails Still Mixing Things Up:
The data presented to this point highlights changes in cybercriminal behavior. Cybercriminals are mainly relying on existing code - with a few minor changes - to build malware variants that can spread quickly and more dangerously. All with the purpose of avoiding detection. This is the malware cocktail.
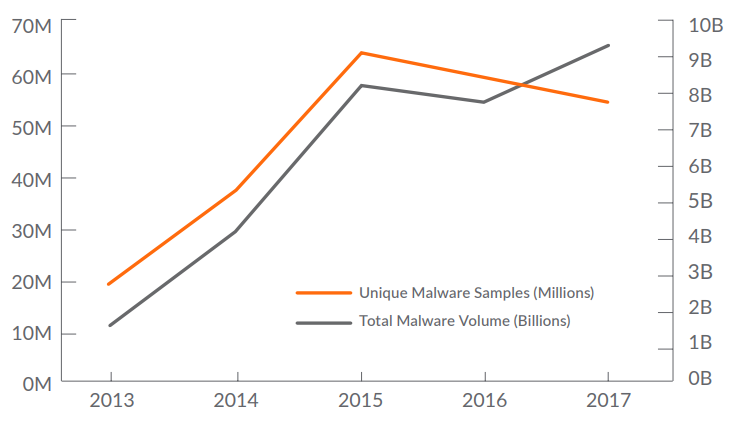
As an example, while the total volume of malware attacks was up, the number of unique malware signatures declined. In 2017, SonicWall collected 56 million unique malware samples in contrast to the 60 million samples discovered in 2016.
For the year, unique malware signatures dipped 6.7 percent from 2016 and 12.5 percent from 2015. However, 2017 levels remain 51.4 percent higher than the 2014 mark.
SonicWall Capture Labs uses machine learning to examine individual artifacts of malware signatures to categorize each as unique or something that already exists. This helps reduce the number of new signatures needed to effectively mitigate known and unknown malware attacks.
The reason? Malicious groups are still using the same malware - with slight tweaks and modifications - as seen in years past. But threat actors aren’t just re-tooling old malware code and launching it haphazardly. While some of that still occurs from ‘script kiddies’ and other less-skilled hackers, innovative authors are refining how they target their victims.
Rise of the Malware Cocktail
Evolving malware tactics
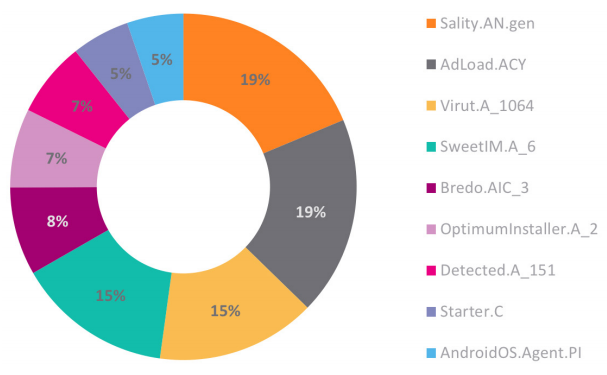
Take Cerber, for example. It’s a Trojan that mainly spreads via email spam, but also leverages exploit kits (EK), such as Magnitude EK in September 2017. It also was one of the top attacks that used encryption to avoid detection. What’s noteworthy about Cerber is its ability to evolve in a short period of time. SonicWall Capture Labs threat researchers were identifying updated versions of Cerber being caught in the wild - as many as two versions a day. These were malware cocktails created by cybercriminals to elude signature-based security solutions. Even more interesting, the new Cerber variants were utilizing seven different tactics to evade detection.xxx
Hits vs. DetectionSignature Detection Malware Hit |
New exploit kits, old code
SonicWall Capture Labs threat researchers aren’t discovering many new exploit kits. What they are finding, however, are EKs that repurpose old code for new gains. Terror, for example, was an exploit kit first noticed in early 2017. Then a new version of the Terror exploit kit appeared, which seemed to be based on code stolen from both the RIG and Sundown exploit kits.xxxi
The Terror landing page consisted of a JavaScript that appeared to be taken from RIG, followed by another script stolen from Sundown. This stolen JavaScript was followed by embedded Flash exploits. There is no obfuscation seen in this exploit kit, and both the landing page and payload are unencrypted. Similarly, the exploit kit Nebula was discovered in February 2017. It was likely a variant of Sundown and spread the DiamondFox and Ramnit malware, among others.xxxii
Agile malware cocktails, coupled with new propagation methods (e.g., NSA exploits, remote desktop protocols, toast overlays), show that some cybercriminals are still at work mixing and matching malware attacks to circumvent defenses, particularly legacy signature-based security approaches.
Top Malware Detection
 IoT, Processor Threats Signal What's to Come:
IoT, Processor Threats Signal What's to Come:
Cybercriminals are pushing new attack techniques into advanced technology spaces, notably the Internet of Things (IoT) and chip processors. These areas are grossly overlooked and unsecured, and present a window of opportunity for successful cyberattacks.
Mitigating Meltdown
In January 2018, a processor vulnerability, known as Meltdown, was published by Google’s Project Zero security team.xxxiii Variants of this issue are known to affect many modern processors. A successful exploit of this vulnerability could allow an attacker to access sensitive information (e.g., passwords, emails, documents) inside protected memory regions on modern processors.
These memory regions are the next key battlegrounds where organizations will combat cybercriminals. To mitigate these chip-based threats, organizations will soon need to implement advanced techniques that can detect and block malware that does not exhibit any malicious behavior and hides its weaponry via custom encryption. This weaponry is exposed in memory for less than 100 nanoseconds, so real-time identification and mitigation is critical.
Modern malware writers implement advanced techniques, including custom encryption, obfuscation and packing, as well as acting benign within sandbox environments, to allow malicious behavior to remain hidden in memory. These techniques often hide the most sophisticated weaponry, which is only exposed when run dynamically and, in most cases, is impossible to analyze in real-time using static detection techniques.
IoT Reaper looming
Since the unwelcomed and unexpected appearance of Mirai and related DDoS attacks in September 2016, the IoT space has been highly active.
The most high-profile evolution of Mirai is IoT Reaper. This variant doesn't leverage weak password policies like Mirai, but rather exploits nine vulnerabilities in various IoT devices. As an example, IoT Reaper, a type of Trojan, integrated LUA execution environments for more complex attacks.
At one point in 2017, SonicWall Capture Labs was recording more than 62,000 IoT Reaper hits each day. Unmitigated, it slowly faded away without being leveraged to launch a widescale attack.
Inspect Deep MemoryA patent-pending technology, the SonicWall Real-Time Deep Memory Inspection (RTDMITM) engine proactively detects and blocks unknown mass-market malware via deep memory inspection. In real time, the engine identifies and mitigates even the most insidious modern threats, including future Meltdown exploits. |
IoT Reaper IPS Hits
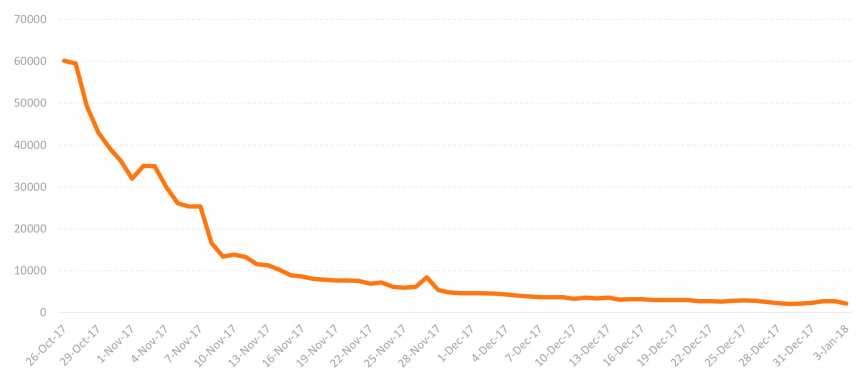
At one point in 2017, SonicWall was recording more than 62,000 IoT Reaper hits each day. SonicWall created and automatically applied nine unique IPS signatures and five GAV signatures to mitigate IoT Reaper.
The Mirai LegacyFirst discovered in late 2016, Mirai is an IoT malware that can be used to launch gigabit-plus DDoS attacks via a zombie botnet created with compromised internetconnected devices (e.g., DVRs, IP cameras, etc.). Until that point, the majority of DDoS prevention solutions couldn’t handle traffic that surpassed 1 Gbps, so many public services and domain name systems (DNS) were knocked offline. Mirai used common factory default usernames and passwords to gain access to connected devices and infect them with malicious code. SonicWall discovered several variants of Mirai that were re-tooled to add new vulnerabilities or target specific devices. Meltdown & Spectre Exploits PDF & Microsoft Office Threats More Infostealers New Ransomware Tricks Surge in Encrypted Attacks Proactive IoT Malware Malicious Cryptocurrency Mining Consumer IoT Attacks Device Control |
Best Practices & Final Takeways:
Each year presents new and interesting developments that define the state of the cyber arms race and cybersecurity industry. These advances drive the actions of each organization, business, government and individual. Unsurprisingly, 2017 was no different.
While threat actors and cybercriminals are sophisticated, agile and well-funded, the public and private sectors are turning the tide in the cyberwar. But it is a war, not just a battle.
To survive the cyberwar, organizations must ensure they’re leveraging the proper security tools, services and solutions that will appropriately protect their brand, data and customers.
What was once a must-have capability two or three years ago could be outdated today. It’s imperative that security solutions, appliances and strategies are continually optimized or evaluated to ensure that they are layered, integrated, intelligent and versatile.
Layered
The best cybersecurity strategies are layered, automatic and dynamic. Security-conscious organizations will deploy a cohesive mix of devices and controls to serve as the fabric of their security posture. This includes next-generation firewalls, email security solutions, real-time cloud sandboxing, secure mobile access controls and wireless access points.
- Layer security across wired, wireless, cloud and mobile networks
- Regularly patch all operating systems, software, network devices and security appliances
- Evaluate the use of cybersecurity insurance to help mitigate risk exposure
Intelligent
Once deployed, this strategy should be dynamic enough - using machine-learning and artificial intelligence - to make real-time decisions against the most advanced and savvy cyberattacks. Intelligence must also extend past technology to include employees, contractors and vendors.
- Use automated cloud sandboxes to identify and analyze unknown cyberattacks (e.g., ransomware, zero-day threat) in real time
- Bolster security via shared intelligence by subscribing to relevant security services from your vendor or solution provider
- Educate employees about cyberattack risks (e.g., phishing, malware) and routinely test awareness
- Investigate the use of real-time deep memory inspection
Integrated & Automated
Still, it takes more than buying siloed point solutions. They should be integrated as the foundation of an automated, realtime breach detection and protection platform, which will link security, intelligence, analytics, management and reporting.
- Deploy next-generation firewalls that leverage shared intelligence and real-time mitigation to protect against advanced cyberattacks
- Implement responsible SSL/TLS decryption and inspection capabilities
- Properly configure gateway anti-virus and intrusion prevention on next-generation firewalls
- Use email security solutions to block email-borne threats
Versatile
To protect their business, brand and data, organizations require critical security capabilities - deployed in an integrated, cohesive manner - across their environments. They should have the power and flexibility to deploy what they want, when they want and where they want to eliminate complexity and potential network vulnerabilities.
- Procure security solutions that match the deployment capabilities and form factors that makes sense for your business
- Build agility through hybrid infrastructures via powerful virtualized cybersecurity controls

